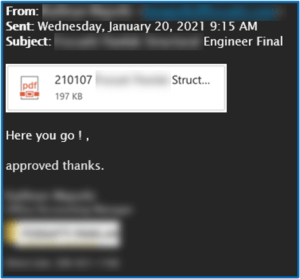
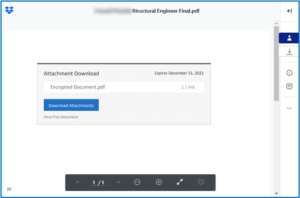
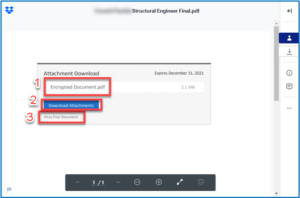
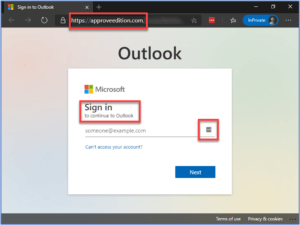
SECURITY CORNER: How to Know If Your Login Credentials Have Been Compromised in a Security Breach
This article is about how to know if your login credentials have been compromised in a security breach and what you can do about it.
As you continue to evaluate your options for using a password manager, and assessing your current security stance, we would like to share an industry-leading security website that tracks company breaches from across the world that will let you know if your email or password has been compromised in a security breach.
But first, let’s define “breach.” A breach is an incident where data is inadvertently exposed. This usually happens because there are insufficient access controls or there are security weaknesses in the software. In either case, it means your personal and/or business information is at risk for misuse.
Where To Check if Your Login Credentials Have Been Compromised in a Security Breach:
 To check if your EMAIL has been compromised, go here: www.haveibeenpwned.com
To check if your EMAIL has been compromised, go here: www.haveibeenpwned.com
To check if your PASSWORD has been compromised, go here: www.haveibeenpwned.com/Passwords
These web pages will check your addresses and passwords against known data that may have become compromised due to company breaches over the past several years. There is no login required and the web interface is easy to use.
What To Do If Your Login Credentials Have Been Compromised in a Security Breach:
After checking your common email addresses and passwords, if you find that your login information has been compromised, we highly recommend making some changes. Review your logins and change the ones using compromised passwords to something unique for the specific site. If your email address was compromised, change the password for that email account too.
The best practice for creating a strong password is to include letters, numbers, special characters, and to make it at least twelve characters long.
How to Prevent Your Login Credentials from Being Compromised in a Security Breach:
Also, now would be an excellent time to start using a password manager, like LastPass, to help keep all these new passwords easy to track and secure.
If you would like guidance or assistance in setting up your firm with a password manager, please let us know. Your team at Sorted Solution is here to help.